A Content Delivery Network (CDN) is a network of servers that delivers digital content quickly and securely to users worldwide. As more services move online, CDN security has become crucial for protecting against cyber threats like data breaches, DDoS attacks, and unauthorized access.
Related video from YouTube
Key Benefits of a Secure CDN
| Benefit | Description |
|---|---|
| Faster Content Delivery | Caching content on servers closer to users reduces data travel distance, improving load times. |
| Improved User Experience | Faster loading times and reduced latency enhance the overall user experience. |
| Increased Reliability | Traffic is distributed across multiple servers, reducing downtime risk. |
| Enhanced Security | Properly configured CDNs protect against cyber threats like DDoS attacks and data breaches. |
Understanding CDN Security Risks
- Data Breaches and Theft: Hacked CDN servers can lead to data breaches, theft of sensitive information, financial losses, and legal issues.
- DDoS Attacks: Distributed Denial of Service attacks can overwhelm servers, causing service disruptions, slow load times, and outages.
- Cache Tampering: Attackers can manipulate cached content to inject malware, steal data, or redirect users to malicious sites.
- Certificate Breaches: Compromised TLS/SSL certificates enable man-in-the-middle attacks and data interception.
- Multi-Tenant Issues: If one client’s account is compromised, it can affect other clients sharing the infrastructure.
Securing Your CDN: Best Practices
- Choose a reputable CDN provider with strong security features like DDoS protection and SSL/TLS encryption.
- Implement Web Application Firewalls (WAFs) to block malicious traffic and attacks.
- Use SSL/TLS encryption to protect data in transit between servers and users.
- Implement access controls like multi-factor authentication and role-based access.
- Regularly update systems and software to protect against known vulnerabilities.
How CDN Security Works
- Encryption and User Verification: SSL/TLS encryption and authentication methods like multi-factor authentication secure data transfers and verify user identities.
- Access Control: Role-based access control and access control lists (ACLs) restrict unauthorized access to CDN resources.
- DDoS Attack Prevention: Traffic monitoring, rate limiting, IP blocking, and content filtering/caching help prevent DDoS attacks.
- Content Filtering: Filters out malicious traffic, requests, and websites based on predefined criteria.
Advanced CDN Security Measures
- Digital Rights Management (DRM): Encrypting content and using watermarking/fingerprinting to prevent unauthorized access and piracy.
- Content Protection: Embedding watermarks, fingerprints, and encryption to deter and detect content theft.
- AI and Machine Learning: Predicting and preventing security threats in real-time using anomaly detection and threat prediction models.
- Monitoring and Analytics: Continuous traffic monitoring and real-time analytics for incident response and performance optimization.
Data Privacy and Compliance
CDNs must follow data privacy laws and regulations like GDPR, CCPA, HIPAA, and PCI-DSS to protect personal and sensitive information. Ensuring compliance involves regular security checks, strong access controls, data encryption, clear data processing agreements, and personnel training.
The Future of CDN Security
- Emerging Technologies: 5G and edge computing will require enhanced encryption, access controls, and new security approaches.
- Evolving Threats: Advanced cyber threats will necessitate AI-driven threat detection, behavioral analysis, and incident response.
- Stakeholder Collaboration: CDN providers, ISPs, and others must collaborate to share threat intelligence, best practices, and resources for enhanced security.
sbb-itb-738ac1e
Understanding CDN Security
What is CDN Security?
CDN Security refers to the measures taken to protect the content and infrastructure of a Content Delivery Network (CDN) from cyber threats. As more services move online, CDNs have become essential for delivering digital content quickly and securely. CDN Security involves various protective measures, such as encryption, access control, DDoS (Distributed Denial of Service) attack mitigation, and data integrity assurance. These measures safeguard the content being delivered to end-users and protect the CDN infrastructure from unauthorized access, data breaches, and other potential threats.
Secure Content Delivery
CDN security plays a vital role in providing a safe and fast web browsing experience. Effective web security requires protection at multiple layers, including the code, web server configuration, hosting, and password creation. CDNs offer built-in security features, such as:
- Distributed Denial of Service (DDoS) Protection: Mitigates DDoS attacks that attempt to overwhelm servers with traffic.
- Web Application Firewalls (WAFs): Filters and blocks malicious web traffic, protecting against common web application vulnerabilities.
- SSL (Secure Sockets Layer): Encrypts data transmitted between the user’s browser and the web server, ensuring secure communication.
By implementing CDN security best practices, businesses and organizations can ensure the secure delivery of digital content to their users, maintaining trust and protecting their reputation.
| Security Feature | Description |
|---|---|
| DDoS Protection | Mitigates Distributed Denial of Service attacks that attempt to overwhelm servers with traffic. |
| Web Application Firewalls (WAFs) | Filters and blocks malicious web traffic, protecting against common web application vulnerabilities. |
| SSL (Secure Sockets Layer) | Encrypts data transmitted between the user’s browser and the web server, ensuring secure communication. |
CDN Security Risks
CDNs handle large amounts of data, making them targets for cyber threats. Understanding these risks is key to protecting content and infrastructure.
Data Breaches and Theft
If a CDN server is hacked, attackers can access and manipulate cached data, leading to:
- Data breaches
- Theft of sensitive information
- Financial losses
- Damage to reputation
- Legal issues
DDoS Attacks
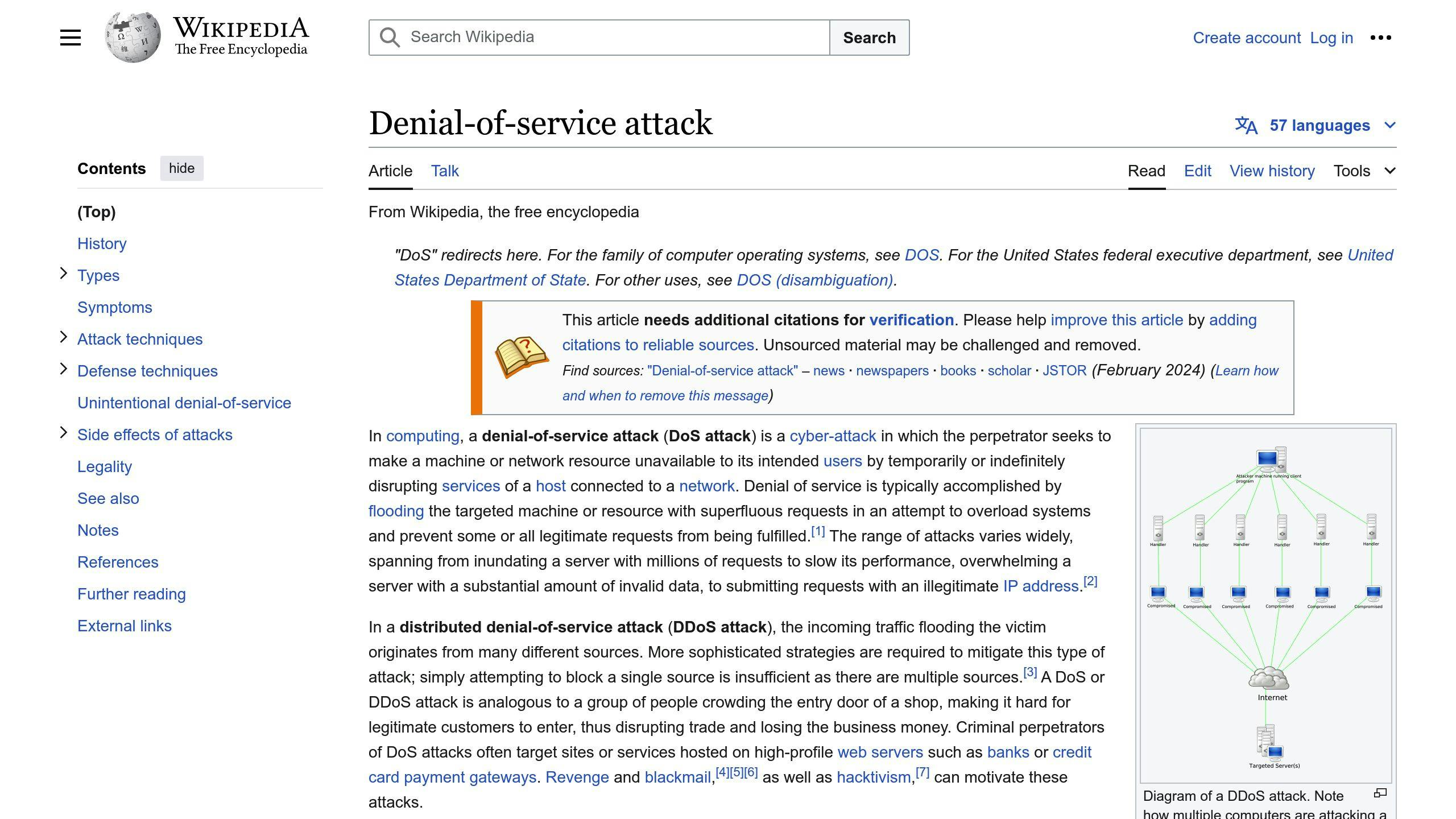
Distributed Denial of Service (DDoS) attacks overwhelm servers with traffic, causing:
- Service disruptions
- Slow load times
- Complete outages
- Poor user experience
- Revenue loss
Cache Tampering
Attackers can manipulate cached content to:
- Inject malware
- Steal data
- Redirect users to malicious sites
This is done by exploiting caching vulnerabilities or compromising the origin server.
Certificate Breaches
If TLS/SSL certificates are compromised, attackers can:
- Intercept and manipulate data
- Perform man-in-the-middle attacks
- Cause data breaches
Multi-Tenant Issues
CDNs often serve multiple clients from the same infrastructure. If one client’s account is compromised, it can affect other clients sharing the infrastructure, leading to broader security risks.
Securing Your CDN
Protecting your CDN from cyber threats is crucial. Here are some best practices to keep your content and infrastructure secure:
Choosing a CDN Provider
When selecting a CDN provider, consider their security track record and the features they offer, such as:
- DDoS protection
- SSL/TLS encryption
- Access control
Look for providers with a strong security and reliability history.
Web Application Firewalls (WAFs)
WAFs analyze incoming traffic and block suspicious requests, preventing attacks like SQL injection and cross-site scripting (XSS). They are essential for protecting against malicious traffic.
SSL/TLS Encryption
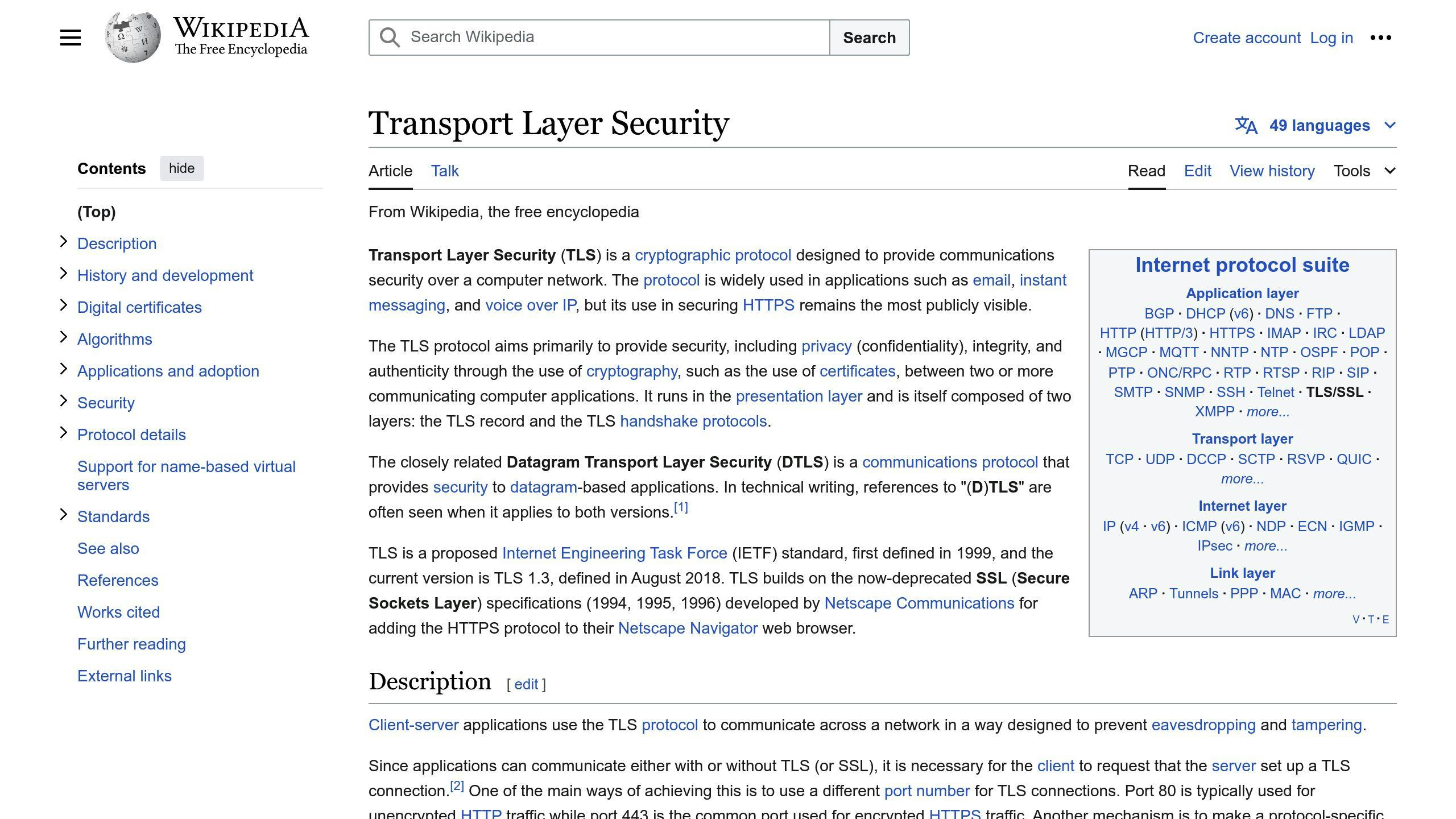
Encrypting data during transmission between the origin server, CDN edge servers, and end-users prevents interception and manipulation of sensitive information.
Access Control
Implementing multi-factor authentication and role-based access control restricts unauthorized access. Only authorized personnel can manage CDN settings and configurations, reducing the risk of human error or unauthorized access.
Software Updates
Regularly updating systems and software protects against known vulnerabilities. Ensure your CDN provider updates their systems and software to prevent exploitation.
CDN Security Comparison
| Security Measure | Advantages | Disadvantages |
|---|---|---|
| WAF | Blocks malicious traffic and attacks | Can be resource-intensive |
| SSL/TLS Encryption | Encrypts data in transit | Can impact performance |
| Access Control | Restricts unauthorized access | Can be complex to implement |
| Software Updates | Protects against known vulnerabilities | Can be time-consuming |
How CDN Security Works
Encryption and User Verification
CDNs use encryption and authentication to secure data transfers and verify user identities:
- SSL/TLS encryption protects data between the origin server, CDN edge servers, and end-users.
- Authentication methods like multi-factor authentication and role-based access control restrict unauthorized access.
Access Control
Access control limits who can access CDN resources:
- Multi-factor authentication and role-based access control restrict access to authorized personnel only.
- Access control lists (ACLs) define permissions and access levels for users and groups.
DDoS Attack Prevention
CDNs use various techniques to detect and stop DDoS attacks:
| Technique | Description |
|---|---|
| Traffic Monitoring | Monitors incoming traffic to identify suspicious patterns. |
| Rate Limiting and IP Blocking | Prevents malicious traffic from overwhelming the network. |
| Content Filtering and Caching | Reduces load on origin and edge servers. |
Content Filtering
Content filtering blocks malicious content and protects users:
- Filters out malicious traffic and requests based on IP addresses, user agents, and other criteria.
- Blocks access to known malicious websites and domains.
- Content Security Policies (CSPs) define which content sources are allowed to execute within a web page.
Security Workflow
- Traffic Monitoring: The CDN monitors incoming traffic in real-time to identify suspicious patterns.
- Threat Analysis: The CDN analyzes the traffic to determine the threat severity and appropriate response.
- Mitigation: The CDN implements measures like rate limiting and IP blocking to prevent the attack from overwhelming the network.
- Content Filtering: The CDN filters out malicious content and requests to protect users and origin servers.
- Reporting and Analytics: The CDN provides reporting and analytics to help customers understand the attack and improve security.
Advanced CDN Security
Digital Rights Management
Digital Rights Management (DRM) helps protect digital content from unauthorized access and piracy. CDNs can use DRM to encrypt content, making it unreadable to unauthorized users. This prevents piracy and theft.
DRM techniques include:
- Encryption: Scrambling content to make it unreadable without proper access.
- Watermarking: Embedding hidden marks to identify content ownership.
- Digital fingerprinting: Creating unique identifiers to track content distribution.
By using DRM, CDNs add an extra layer of security for digital content, preventing unauthorized access and piracy.
Content Protection
Content protection involves embedding marks or identifiers into digital content to deter and detect theft. CDNs can use techniques like:
- Watermarking: Embedding hidden marks to identify content ownership.
- Fingerprinting: Creating unique identifiers to track content distribution.
- Encryption: Scrambling content to make it unreadable without proper access.
By embedding marks or identifiers, CDNs can discourage content theft and detect unauthorized use.
AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) help predict and prevent security threats in real-time. CDNs can use AI and ML to:
- Detect anomalies: Identify unusual traffic patterns that may indicate threats.
- Predict threats: Anticipate potential threats based on historical data and traffic patterns.
- Respond in real-time: Detect and respond to security threats as they happen.
Using AI and ML helps CDNs improve security and respond to threats more effectively.
Monitoring and Analytics
Continuous monitoring and real-time analytics are crucial for advanced CDN security. CDNs can use monitoring and analytics to:
| Technique | Purpose |
|---|---|
| Traffic monitoring | Track traffic patterns to identify unusual activity. |
| Incident response | Respond to security incidents as they happen. |
| Performance optimization | Improve security and reduce latency by optimizing CDN performance. |
Data Privacy and Compliance
Privacy Laws
CDNs must follow various data privacy laws and rules. Some key ones include:
| Law/Regulation | Region | Purpose |
|---|---|---|
| General Data Protection Regulation (GDPR) | European Union | Protect personal data |
| California Consumer Privacy Act (CCPA) | California, USA | Protect consumer privacy |
| Health Insurance Portability and Accountability Act (HIPAA) | United States | Safeguard health information |
| Payment Card Industry Data Security Standard (PCI-DSS) | Global | Secure payment card transactions |
These laws aim to protect people’s personal information and ensure organizations handle sensitive data responsibly.
Ensuring Compliance
To follow data privacy rules, CDNs can:
- Conduct regular security checks and risk assessments
- Use strong access controls and authentication
- Encrypt data in transit and at rest
- Have clear data processing agreements with customers
- Provide guidelines on data handling and processing
- Train personnel on data privacy regulations
Future of CDN Security
Emerging Technologies
As 5G and edge computing become more widespread, CDNs will face new security challenges. With 5G’s faster speeds and lower latency, plus more connected devices, CDNs must implement stronger security measures like enhanced encryption and access controls. Edge computing brings data storage and processing closer to users, requiring new security approaches.
Evolving Threats
Cyber threats are getting more advanced, with attackers using AI tools for targeted attacks. CDNs must invest in AI-driven threat detection, behavioral analysis, and incident response to stay ahead. They also need to prioritize security awareness and training for employees and customers to identify and respond to new threats.
Stakeholder Collaboration
| Collaboration Area | Purpose |
|---|---|
| Threat Intelligence Sharing | Exchange information on emerging threats |
| Best Practice Sharing | Learn from each other’s security strategies |
| Resource Sharing | Pool resources to enhance security |
CDN providers, ISPs, and other stakeholders must collaborate to enhance security and protect against complex cyber threats. By working together, they can address emerging risks and ensure online content’s security and integrity.
Conclusion
Key Points
Here are the key points to remember about CDN security:
- CDNs face risks like data breaches, DDoS attacks, cache tampering, certificate issues, and multi-tenant problems.
- To secure your CDN:
- Choose a reputable provider with strong security features.
- Use access controls and encryption.
- Monitor traffic and keep software updated.
- New technologies like 5G and edge computing will bring new security challenges.
- Collaboration between CDN providers, ISPs, and others is crucial to enhance security.
Final Thoughts
CDN security is vital for safe online content delivery. As more content moves online, CDNs play a critical role in protecting digital assets. By prioritizing CDN security, businesses can:
- Safeguard their online presence
- Protect customer data
- Maintain trust in the digital economy
Stay ahead of emerging threats to ensure the security of your online assets. A secure CDN is essential for reliable content delivery.
| Benefit | Description |
|---|---|
| Online Presence | Safeguard your online presence |
| Data Protection | Protect customer data and information |
| Trust | Maintain trust in the digital economy |
FAQs
What is CDN security?
CDN security refers to the measures taken to protect the content and infrastructure of a Content Delivery Network (CDN) from cyber threats. As more services move online, securing CDNs has become crucial for safe content delivery.
What are the vulnerabilities of a CDN?
CDNs can be vulnerable to:
- Data breaches: If a CDN server is hacked, attackers can access and manipulate cached data.
- DDoS attacks: Distributed Denial of Service attacks can overwhelm CDN servers, causing service disruptions and outages.
- Cache tampering: Attackers may manipulate cached content to inject malware or redirect users to malicious sites.
- Certificate breaches: Compromised TLS/SSL certificates can enable man-in-the-middle attacks and data interception.
- Multi-tenant issues: If one client’s account is compromised, it can affect other clients sharing the same infrastructure.
Can a CDN be compromised?
Yes, CDNs can be compromised. Since CDNs store copies of web content, including potentially sensitive data, across various servers, a breach in any of these servers can lead to a data breach.
What are the considerations for CDN security?
Key considerations for CDN security include:
- Preventing data theft, loss, or inaccuracy
- Avoiding service blockages or reduced bandwidth
- Maintaining user efficiency and fast speeds
- Safeguarding the online presence and customer data
- Maintaining trust in the digital economy
What is a secure CDN?
A secure CDN is one that protects data throughout the delivery process from theft and loss, without compromising user experience. It involves implementing robust security measures like:
| Security Measure | Purpose |
|---|---|
| Encryption | Scrambling data to prevent unauthorized access |
| Access Controls | Restricting access to authorized users only |
| DDoS Mitigation | Preventing Distributed Denial of Service attacks |
This ensures the safe delivery of content to end-users.
Related posts
- Cloud Content Protection: Ultimate Guide 2024
- Dynamic Encryption Best Practices for Content Protection
- 10 DAM Security Best Practices to Safeguard Digital Assets
- Protect Your Content from Unauthorized Sharing

