To protect digital games from piracy and secure revenue streams, game developers must implement an effective Digital Rights Management (DRM) strategy. Here are the 10 key features for effective DRM in game distribution:
- Strong File Encryption – Encrypt game files and DRM components using AES-256, the industry-standard encryption method, to prevent unauthorized access and piracy.
- Multi-Platform Support – Ensure the DRM system works seamlessly across different gaming platforms like PCs, consoles, and mobile devices to reach more players while protecting against piracy.
- User Authentication and Access Control – Verify users’ identities and control access levels to prevent unauthorized use through methods like online activation, hardware binding, single-use keys, subscription-based access, and tiered access.
- License Management System – Centralize license management for easy tracking, revocation, and customer support. Offer flexible licensing options like time-based, feature-based, and concurrent usage licenses.
- Anti-Tamper and Anti-Debug Measures – Prevent file tampering and reverse engineering through code obfuscation, integrity checks, encryption, anti-debugging techniques, dynamic code loading, and white-box cryptography.
- Online Verification and Updates – Regularly check license validity and update the DRM system to address security threats and vulnerabilities.
- Hardware-Based Protection – Use secure enclaves, trusted execution environments, and other hardware solutions for an extra layer of protection against piracy and attacks.
- Logging and Analytics – Monitor user behavior, system performance, and security vulnerabilities by analyzing DRM data and logs.
- User-Friendly Experience – Balance security with usability by implementing user-friendly interfaces, intuitive login mechanisms, adaptive security levels, minimized authentication steps, silent authentication, and flexible licensing options.
- Legal and Regulatory Compliance – Ensure compliance with laws like the Digital Millennium Copyright Act (DMCA) and the General Data Protection Regulation (GDPR) by regularly auditing DRM systems, preventing circumvention, being transparent about data usage, establishing data handling procedures, and staying updated on regulations.
Related video from YouTube
Strong File Encryption
Encrypting game files and DRM components is crucial for preventing piracy and unauthorized access. Here’s what you need to know:
AES-256: The Industry Standard
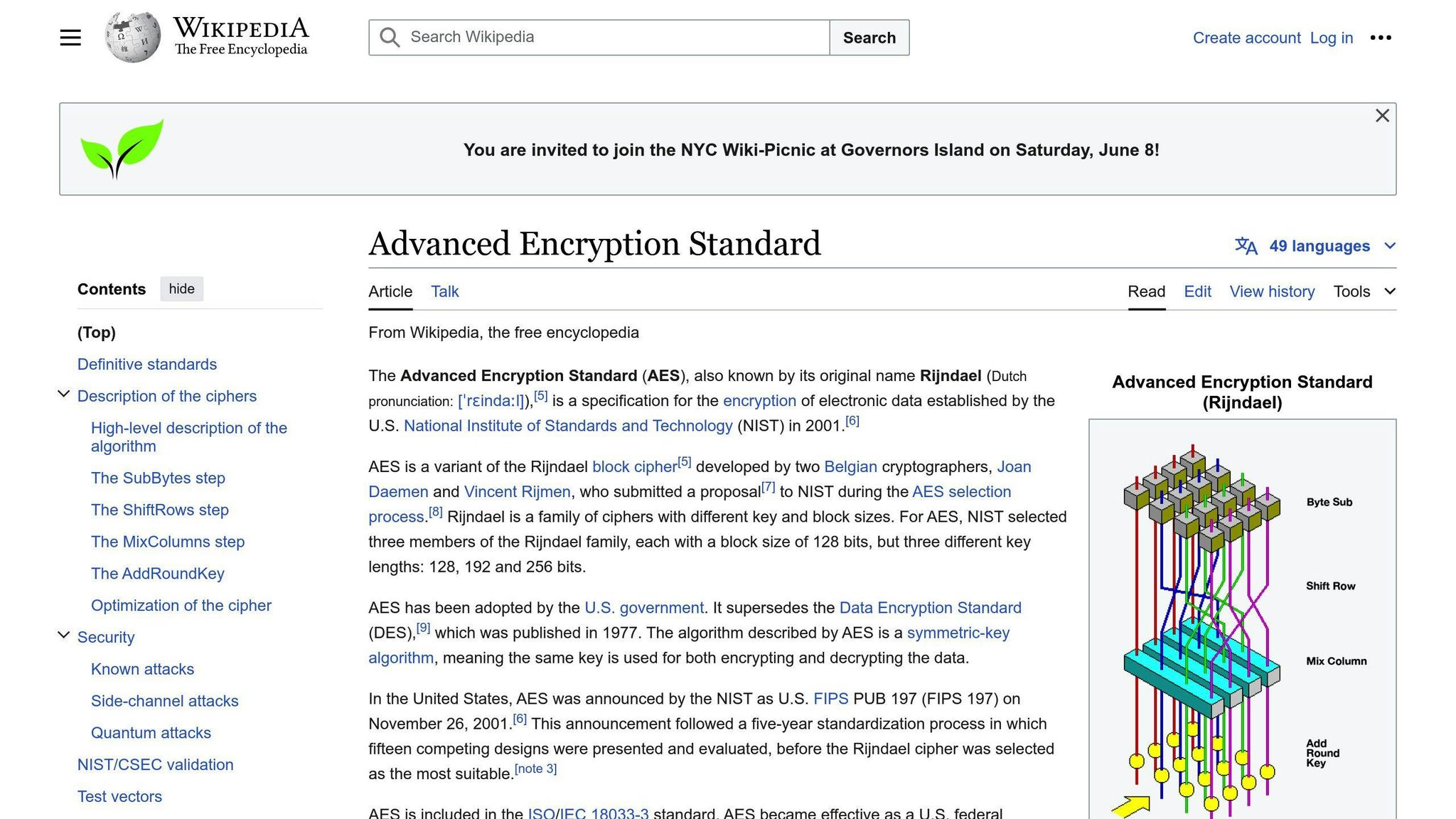
AES-256 is the widely accepted standard for secure encryption. It uses a 256-bit key to encrypt and decrypt data, making it virtually unbreakable. Game developers use AES-256 to protect sensitive game data and DRM components from piracy and intellectual property theft.
Encrypt Game Data and DRM Parts
It’s not enough to encrypt just the game data. DRM components like encryption keys, license files, and other sensitive data must also be encrypted. This comprehensive approach prevents unauthorized access and ensures your digital content is protected throughout distribution. By encrypting both game data and DRM parts, you maintain control over your content and prevent revenue loss due to piracy.
| Encryption Target | Description |
|---|---|
| Game Data | Encrypting the game files themselves is essential. |
| DRM Components | Encryption keys, license files, and other sensitive DRM data must also be encrypted. |
Implementing strong file encryption with AES-256 is critical for protecting game files and DRM components. By encrypting both game data and DRM parts, you can safeguard your digital content against piracy and intellectual property theft.
Multi-Platform Support
Supporting Different Platforms
Your Digital Rights Management (DRM) system should work smoothly across various gaming platforms and devices. This includes:
- PCs
- Consoles
- Mobile devices
The DRM system needs to encrypt and decrypt game data, authenticate users, and manage licenses on different operating systems and hardware setups. By supporting multiple platforms, you can reach more players while protecting your game from piracy and unauthorized access.
Multi-Platform DRM Challenges
Implementing DRM across various platforms can be complex. Here are some key challenges:
1. Compatibility
Ensuring the DRM system works with different hardware and software configurations.
2. Security Levels
Handling varying levels of security and encryption supported by different platforms.
To overcome these challenges, choose a DRM solution that is:
- Flexible
- Scalable
- Able to adapt to different platform requirements
| Challenge | Description |
|---|---|
| Compatibility | Ensuring the DRM system works with different hardware and software configurations. |
| Security Levels | Handling varying levels of security and encryption supported by different platforms. |
Solution Requirements
| Requirement | Description |
|---|---|
| Flexibility | The DRM solution should be flexible enough to work across platforms. |
| Scalability | It should be scalable to accommodate future platform updates and changes. |
| Adaptability | The solution should adapt to different platform requirements for security and encryption. |
User Authentication and Access Control
Verifying users and controlling access are key parts of a strong DRM system. These features ensure only authorized people can play your game, preventing piracy and unauthorized use.
Secure User Verification
Securely verifying users prevents unauthorized access to your game. Methods include:
- Online activation: Users activate the game online, verifying their identity and ensuring they have a legitimate copy.
- Hardware binding: The game is tied to the user’s device, making it harder for pirates to access it on other devices.
These methods can be used alone or together for added security.
Access Control Methods
Access control determines how users can access your game and what features they can use. Options include:
| Access Control Method | Description |
|---|---|
| Single-use keys | Each user gets a unique key that can only activate the game once. |
| Subscription-based access | Users pay a fee to access the game for a set period (e.g., monthly or yearly). |
| Tiered access | Different access levels offer additional game features or content. |
Choose an access control method based on your game’s needs and business model. With robust access control, only authorized users can access your game, reducing piracy risk.
License Management System
A strong license management system is key for effective DRM in game distribution. This system allows game developers to issue, revoke, and track game licenses, ensuring only authorized users can access the game.
Centralized License Management
A centralized license management system provides a single platform for managing game licenses. This approach offers:
- Easy license tracking: Developers can monitor license usage and detect unauthorized activity.
- Streamlined license revocation: Revoking licenses is straightforward, preventing unauthorized access.
- Improved customer support: Developers can quickly resolve licensing issues, reducing frustration.
Flexible Licensing Options
The licensing model supports various business models:
| Licensing Option | Description |
|---|---|
| Time-based licenses | Licenses are valid for a specific period, allowing users to access the game for a limited time. |
| Feature-based licenses | Licenses grant access to specific game features or content, allowing users to customize their experience. |
| Concurrent usage licenses | Licenses allow multiple users to access the game simultaneously, ideal for multiplayer games. |
Anti-Tamper and Anti-Debug Measures
Preventing unauthorized access and changes to game files and the DRM system is crucial. Here’s how developers can achieve this:
Stopping File Tampering
To stop people from modifying game files, developers can use:
- Code obfuscation: Making the source code harder to understand, preventing reverse engineering.
- Code integrity checks: Verifying the code hasn’t been changed using checksums and hash functions.
- Encryption: Encrypting key software parts and firmware to block unauthorized access.
Blocking Reverse Engineering
To prevent people from analyzing and cracking the code, developers can use:
| Anti-Debugging Technique | Description |
|---|---|
| Detect and respond to debugging | Make it harder for attackers to analyze the code. |
| Dynamic code loading | Load parts of the code during runtime, making analysis difficult. |
| White-box cryptography | Design secure algorithms that remain secure even if attackers access the code. |
Protecting Game Files and DRM
| Protection Method | Description |
|---|---|
| Code obfuscation | Modify the source code to make it harder to understand. |
| Code integrity checks | Verify the code hasn’t been tampered with using checksums and hashes. |
| Encryption | Encrypt essential software components and firmware. |
| Anti-debugging techniques | Detect and respond to debugging activities. |
| Dynamic code loading | Load code parts dynamically during runtime. |
| White-box cryptography | Design secure algorithms that remain secure even if attackers access the code. |
sbb-itb-738ac1e
Online Verification and Updates
Periodic License Checks
Game developers should regularly check if game licenses are valid and not revoked. This process involves:
- Checking licenses against a central database through a secure online connection.
- Ensuring the license check is seamless and doesn’t disrupt the user experience.
Regular license checks prevent unauthorized game access and reduce piracy risks.
Updating the DRM System
Keeping the DRM system updated is crucial to stay ahead of potential security threats or exploits. Updates may include:
- Enhancing encryption algorithms
- Improving access controls
- Addressing new security vulnerabilities
By updating the DRM system regularly, game developers can maintain robust security and protect their games from piracy.
Other online verification methods to consider:
| Method | Description |
|---|---|
| Real-time license checks | Checking licenses in real-time to ensure validity and prevent revoked licenses from accessing the game. |
| IP blocking | Blocking access from known pirate IP addresses or regions. |
| Device fingerprinting | Identifying and blocking devices used for pirating the game. |
Hardware-Based Protection
Hardware-based protection adds an extra security layer for game distribution. It uses special hardware parts to protect sensitive data and block unauthorized access. This approach offers higher protection than software-based DRM solutions.
Hardware Protection Options
One option is secure enclaves – isolated areas inside a processor that provide a secure space for sensitive tasks. Another is trusted execution environments (TEEs) – secure areas within a system-on-chip (SoC) that ensure data privacy and integrity. These hardware solutions can protect game licenses, encryption keys, and other sensitive info.
Hardware vs. Software DRM
Hardware-based DRM has benefits over software-based:
| Hardware-Based | Software-Based |
|---|---|
| More resistant to tampering and reverse engineering, making it harder for pirates to bypass | Less secure against tampering and reverse engineering |
| Can offload intensive tasks like encryption/decryption from the CPU, improving performance | CPU handles all tasks, potentially impacting performance |
| Extra layer of protection against attacks like side-channel and fault injection | Lacks hardware-level protection against certain attacks |
However, hardware-based DRM also has downsides:
| Hardware-Based | Software-Based |
|---|---|
| More expensive to implement | Lower implementation costs |
| More complex, requiring specialized expertise and resources | Less complex to implement and manage |
Logging and Analytics
Tracking DRM events and user activities helps identify potential security issues. This includes monitoring license requests, login attempts, and file access. By watching user behavior, game developers can detect suspicious activity like unauthorized access or tampering.
Analyzing DRM Data
Examining DRM data provides insights into user behavior, system performance, and security vulnerabilities. This information can help improve the DRM system, enhance user experience, and optimize resource use. For example, analyzing license request patterns can help game developers streamline their license management system, reducing delays and improving overall performance.
| Data Analysis | Benefits |
|---|---|
| User Behavior | Detect suspicious activities like unauthorized access or tampering |
| System Performance | Identify areas for improvement and optimization |
| Security Vulnerabilities | Uncover potential weaknesses and address them proactively |
| Example | Description |
|---|---|
| License Request Patterns | Analyzing these patterns can help optimize the license management system, reducing latency and improving performance. |
User-Friendly Experience
Providing a smooth experience for legitimate users is vital for game distribution. The DRM system should strike a balance between security and usability, ensuring it doesn’t hinder authorized players.
Balancing Security and Ease of Use
To achieve this balance, developers can:
- Implement a user-friendly interface that simplifies the authentication process, reducing friction.
- Use intuitive login mechanisms and clear instructions.
- Adjust security levels based on user behavior and risk profiles, avoiding unnecessary restrictions.
Minimizing User Friction
To further reduce friction, developers can:
- Avoid excessive authentication steps, like frequent login prompts or password requests.
- Implement silent authentication mechanisms that operate in the background.
- Provide flexible licensing options, allowing users to access games across multiple platforms and devices.
| Strategy | Description |
|---|---|
| User-Friendly Interface | Simplify authentication, reducing friction for authorized users. |
| Intuitive Login | Use clear login mechanisms and instructions. |
| Adaptive Security | Adjust security levels based on user behavior and risk profiles. |
| Minimize Authentication Steps | Avoid excessive login prompts or password requests. |
| Silent Authentication | Implement background authentication for a seamless experience. |
| Flexible Licensing | Allow users to access games across multiple platforms and devices. |
Legal and Regulatory Compliance
Following laws and industry rules is crucial when using DRM for game distribution. Not complying can lead to legal issues, damage your reputation, and cause financial losses.
Key Laws and Standards
The Digital Millennium Copyright Act (DMCA) is an important law affecting DRM. The DMCA’s anti-circumvention rule prohibits bypassing technological protection measures. Game developers must ensure their DRM systems comply with this rule. Additionally, laws like the General Data Protection Regulation (GDPR) impact how user data is handled and protected, which is relevant for DRM implementation.
Ensuring Compliance
To follow the law, game developers should:
- Regularly check for vulnerabilities in their DRM systems
- Implement measures to prevent bypassing technological protection measures
- Be transparent about data collection and usage, providing clear information to users
- Have procedures for handling user data and responding to data breaches
- Stay updated on changing regulations and industry standards, adapting their DRM systems accordingly
| Compliance Step | Description |
|---|---|
| Regular Audits | Check for vulnerabilities in DRM systems |
| Prevent Circumvention | Implement measures to stop bypassing technological protection measures |
| Transparency | Provide clear information to users about data collection and usage |
| Data Handling Procedures | Establish procedures for handling user data and responding to data breaches |
| Stay Updated | Adapt DRM systems to changing regulations and industry standards |
Conclusion
Protecting digital games from piracy and securing revenue streams is crucial. By implementing these 10 key features, game developers can build an effective Digital Rights Management (DRM) strategy:
1. Strong File Encryption
Encrypt game files and DRM components using AES-256, the industry-standard encryption method. This prevents unauthorized access and piracy.
2. Multi-Platform Support
Ensure the DRM system works seamlessly across different gaming platforms like PCs, consoles, and mobile devices. This allows reaching more players while protecting against piracy.
3. User Authentication and Access Control
Verify users’ identities and control access levels to prevent unauthorized use. Methods include online activation, hardware binding, single-use keys, subscription-based access, and tiered access.
4. License Management System
Centralize license management for easy tracking, revocation, and customer support. Offer flexible licensing options like time-based, feature-based, and concurrent usage licenses.
5. Anti-Tamper and Anti-Debug Measures
Prevent file tampering and reverse engineering through code obfuscation, integrity checks, encryption, anti-debugging techniques, dynamic code loading, and white-box cryptography.
6. Online Verification and Updates
Regularly check license validity and update the DRM system to address security threats and vulnerabilities.
7. Hardware-Based Protection
Use secure enclaves, trusted execution environments, and other hardware solutions for an extra layer of protection against piracy and attacks.
8. Logging and Analytics
Monitor user behavior, system performance, and security vulnerabilities by analyzing DRM data and logs.
9. User-Friendly Experience
Balance security with usability by implementing user-friendly interfaces, intuitive login mechanisms, adaptive security levels, minimized authentication steps, silent authentication, and flexible licensing options.
10. Legal and Regulatory Compliance
Ensure compliance with laws like the Digital Millennium Copyright Act (DMCA) and the General Data Protection Regulation (GDPR) by regularly auditing DRM systems, preventing circumvention, being transparent about data usage, establishing data handling procedures, and staying updated on regulations.

